TryHackMe [Advent of Cyber] [Day 4]-> Scanning
In order to detect live hosts, ports, and services, learn the operating system of the target system, and spot vulnerabilities and network…
In order to detect live hosts, ports, and services, learn the operating system of the target system, and spot vulnerabilities and network threats, a set of techniques known as scanning must be used. The majority of the time, these scans are automatic and reveal potential vulnerabilities. Black hat hackers can use scanning to gather sensitive information.
TYPES OF SCANNING
Passive Scanning: This method involves scanning a network without directly interacting with the target device. Capturing and reading through network data.
Active Scanning: This is the intentional scanning of websites, endpoints, and infrastructure for the purpose of stealing sensitive information.
SCANNING TECHNIQUES
Network Scanning
Port Scanning
Vulnerability Scanning
SCANNING TOOLS
Nmap
Nikto
fuzz
gobuster
Burpsuite ( has a GUI) etc.
THE CHALLENGE
Start your machine up top like usual, copy the IP address and use your file explorer to access the samba share. ( I am using the attack box, setting up ovpn is a bit tiring). To log in to the samba share, we use the credentials we found yesterday.
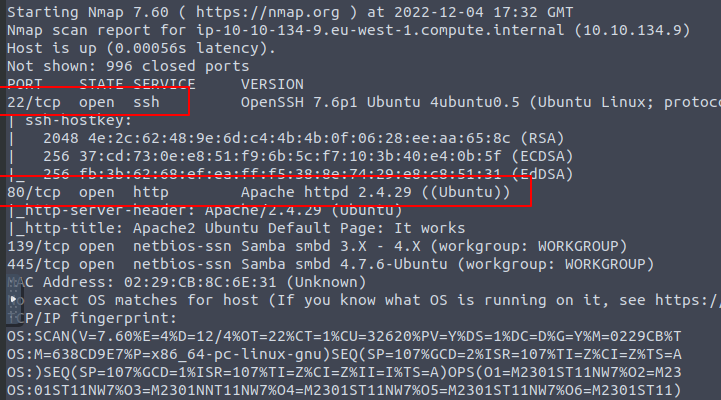
You could do a quick Nmap scan to get questions 1 and 2. Run
nmap -A $IP. You should get an output like the one below.
With this, you have the answers to questions 1 and 2.
HTTP runs on port 80, so just pick the service running on that port.
ssh is the normal service that runs on port 22 as this output confirms.
Enter
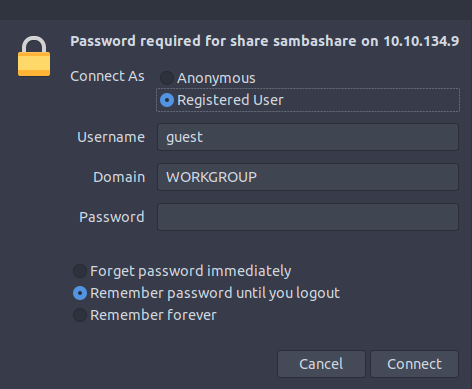
smb://$IP/in the search-like bar of your file explorer. ( Open the attack box in a separate tab for easy copy and paste).
A login form should pop up.
Change to Registered User.
Fill in the DB_USER->Username, DB_PASSWORD->Password, and DB_HOST->Domain that is in this file that we found yesterday.
You will log in and see three folders. Go into admins, you will find the flag inside flag.txt
You will find the password of santahr inside userlist.txt. Both files are in the admins folder.
And that’s it for today.
Secundum Allos Parakletos